Introduction
TCP Chimney Offload Overview
TCP Chimney Offload is a networking technology that helps transfer the workload from the CPU to a network adapter during network data transfer. In Windows Server 2008 and 2008 R2, TCP Chimney Offload enables the Windows networking subsystem to offload the processing of a TCP/IP connection to a network adapter that includes special support for TCP/IP offload processing. TCP Chimney Offload is available in all versions of Windows Server 2008, Windows Server 2008 R2 and Windows Vista. Both TCP/IPv4 connections and TCP/IPv6 connections can be offloaded if the network adapter supports this feature.
More Information
We have come across various problems at customer sites where their ISA, TMG or UAG was behaving in a very strange way. The configuration within the management console seemed to be OK, and all other network components with which the ISA / TMG / UAG Firewall communicating with also seemed to be configured just fine. Still, we’d see strange problems like:
· OWA Web Publishing Rules performing very, very poorly
· PPTP VPN access failed to establish a connection, while L2TP did not experience any problems.
· Adding a second site-to-site VPN tunnel caused the existing VPN tunnel to go down, and no VPN connectivity was possible until the new tunnel was removed from the configuration.
· SMTP server publishing returned lots of failed connection attempts. Some mail would come through, but a lot of mail just failed to be delivered.
Over time we realize that all of these problems were caused by advanced Network card features that are supported in newer versions of Windows. ISA, TMG and UAG are sometimes unable to work properly if these options are enabled. Somewhere deep within the Microsoft documentation these options are mentioned, with the advice to turn all these options off.
Issue
Issue with slow connectivity to UAG portals, end point scanning and general behaviour issues
Resolution or Work Round
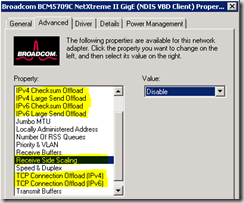
Disable TCP Offload
Please be aware that when modifying the network card, you will lose connectivity to the server for a short period of time and I would recommend that you can get console access to the server
The following configuration should be added to the registry:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Tcpip\Parameters]
“EnableRSS”=dword:00000000
“EnableTCPA”=dword:00000000
“EnableTCPChimney”=dword:00000000
“EnableSecurityFilters”=dword:00000000
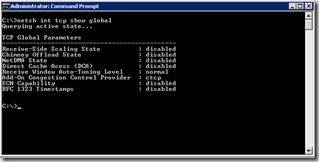
To confirm the settings use the following command - netsh int tcp show global
The output should look something like this:
If receive side scaling and/or chimney offloading are enabled, you can disable them with the following commands:
netsh int tcp set global chimney=disabled
netsh int tcp set global rss=disabled